M. Yusuf Manshur
My expertise spans dashboard monitoring, system integration, and significantly contributed to transactional data orchestration systems.
I am committed to continuous learning about backend development and exploring any cutting-edge technologies through my GitHub
For further discussion, feel free to reach out to me via LinkedIn
Privy Customization: TourID x ASITA




Role: Back-End Engineer
Duration: 7 months
TourID is a tour-agent platform designed to facilitate transactions between travelers and Indonesian travel agents. All participating agents are members of the Association of Indonesian Tours and Travel Agencies (ASITA) and hold digital certificates issued by Privy.
Tech Stack
- Backend Language: Go-lang
- Database: PostgreSQL
- Cloud Storage: Google Cloud Storage
- CI/CD & Orchestration: Jenkins, Docker, Kubernetes
- APM: Datadog
Challenges
When working on this project, a key challenge was understanding and adapting to the existing code from previous development, along with the current business processes and features, before any improvement or fixes could begin.
Contributions
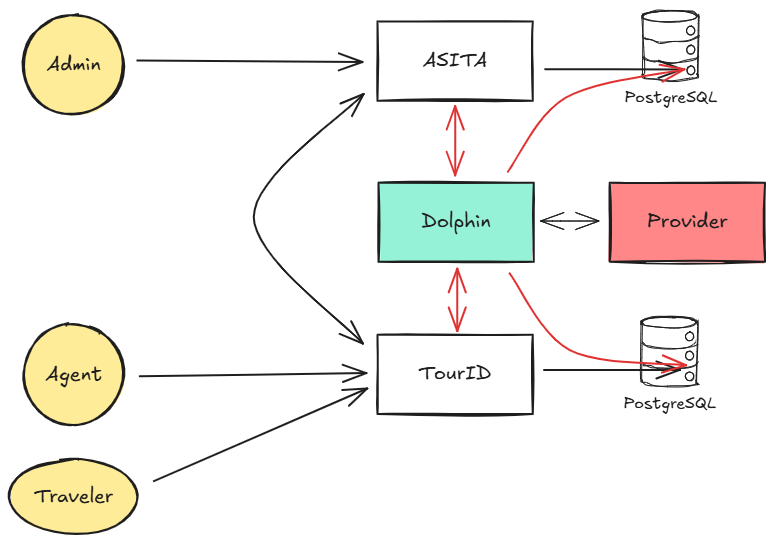
During that process, we found we needed to redesign the architecture, which involved:
-
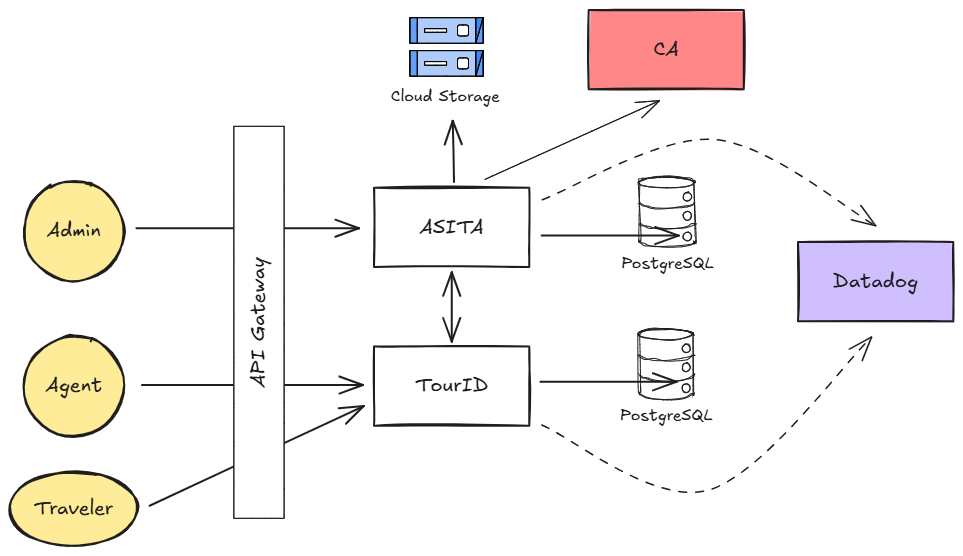
Adding an API Gateway
Previously, i.e. applications like the Tour dashboard had to go through the Tour-backend instead of Verifier-backend service to get document data.
With the API Gateway, the front-end can now directly access data from the relevant source.
The API Gateway also acts as an abstraction layer for internal and external communication, significantly improving security.
-
Eliminating Potential Bottlenecks
Originally, the Tour and Verifier dashboard’s authentication processes relied on a central ‘Dolphin’ authentication service. The idea was to centralize authentication to be independent and reusable across all applications (TourID landing, TourID, and ASITA dashboard), especially when integrating third-party authenticators like Privy.
However, Dolphin wasn’t directly used by the front-end; it still had to go through each related service. This created a “tightly coupled” service with shared-database and circular dependencies. Eliminating Dolphin became the best solution to reduce risk and development effort.
Trade-off: Duplicated authentication modules across all services lead to significant maintenance overhead, particularly with third-party integrations. This structure necessitates redundant implementation whenever a new authentication provider is introduced.
-
Handling PII (Personally Identifiable Information) Data
We needed special handling for PII due to user terms and conditions and Privy’s compliance as a personal data manager. Examples of PII include ID cards, tax IDs, and selfies. We first identified and categorized PII data, making it configurable via environment variables.
Then, we created a dedicated bucket in Google Cloud Storage for this data, with security and privacy adjusted to meet feature requirements.
Capabilities Demonstrated
- Proficient in redesigning microservices architecture, enhancing service choreography to boost communication reliability and system maintainability.
- Experienced in designing and implementing API Gateway to centralize API management, strengthening security and maintainability.
- Adept at integrating observability tools like Datadog to enable thorough system monitoring and performance insights.
- Knowledgeable in implementing compliance measures to protect Personally Identifiable Information (PII) and ensure regulatory adherence.
Architecture
Documentation
Related articles: